Streamlined Security for Fast-Paced Distribution Hubs
Optimizing protection for goods in motion and assets at rest
iS3 Tech Services, Your Trusted Partner in Distribution Center Security and Communication Solutions

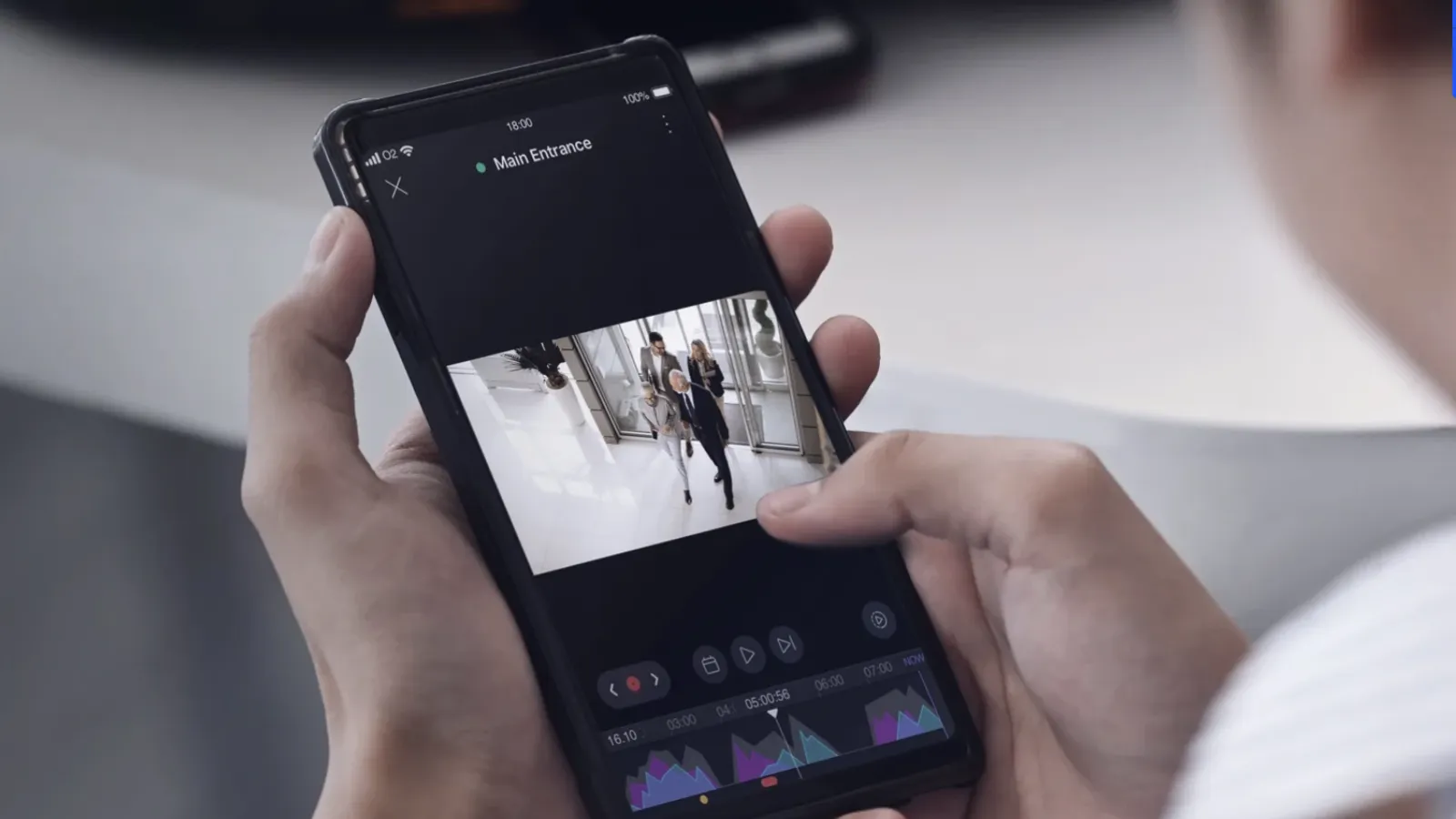
Distribution centers are the backbone of supply chains, where timely operations meet stringent security needs. With iS3's integrated approach, we combine cutting-edge video surveillance with robust access control measures, ensuring a seamless blend of security and operational efficiency. Our specialized solutions are tailored to uphold the integrity of these hubs, bolstering both productivity and peace of mind.

Hear What Our Clients Have to Say
Industry-Specific Queries: Insights Tailored to Your Sector
Q
How does your video surveillance enhance distribution center operations?
Q What measures do you have for visitor management in large distribution centers?
Q Can the access control system integrate with platforms like Azure or other company identity management solutions?
Q
Do you offer real-time alerts for potential security breaches?
Yes, our systems are designed to send real-time alerts in case of unauthorized access attempts, perimeter breaches, or any other suspicious activities. This ensures that immediate action can be taken to address any potential threats.